Welcome back my aspiring white hat hackers to this series on Database Hacking.

In the first installment in this series, we learned the fundamentals of databases including the Structured Query Language or SQL. This is the language of databases. The primary method of hacking databases is to inject this SQL into web forms and other applications that use a backend database. Nearly every application on the web uses a backend database for such things as authentication, e-commerce, email, etc

The diagram above attempts to illuminate the process of SQL Injection. Note that the Attacker enters data into a web form, it goes out to the Internet through the Firewall (the firewall must be open to the web form), to the Web Server, then the application server and from there to the database server. This is the most common form of database hacking. The key here is knowing what SQL commands to enter the web form to affect the database in a way that is useful to you.
Abusing SQL
In this article, I want to teach you the basics of how this language can be abused to get to the underlying database and gain authentication, DoS the database or extract the data.
Most of the simple techniques I will demonstrate here will no longer work against modern applications, but we need to start somewhere and the principles are the same, albeit more sophisticated, in modern systems. In subsequent articles in this series, we will move to increasingly more sophisticated and EFFECTIVE SQL injection techniques.
Authentication
As you will remember from my first article in this series, the basic SQL query looks like this;
SELECT <columns>
FROM <table>
WHERE <conditions>
This basic query can be used for authentication purposes. Imagine a database that has every user with their username and password in a table named "USERS". We could authenticate our users by asking them for their username and password and then checking the database table to see if they match. Such a query would look like this when the user entered into the authentication form;

SELECT USERNAME, PASSWORD
FROM USERS
WHERE USERNAME ='OTW' AND PASSWORD = 'HackersArise'
Notice that in the WHERE clause with the conditions, we have a logical AND. This means that both conditions must evaluate to TRUE for the user to successful authenticate and gain access to the system. If either is false, then the query evaluates to false and the user does not get authenticated and entry to the system.
This is the way most systems authenticate users.
Notice that in both the username field and the password field the entries are enclosed with a single quote ('). This is standard in SQL when using strings (text) in the WHERE clause.
Getting Past the Authentication
It is also important to note that in SQL, the double dash ( --) acts as a comment character. This means that if a -- appears, everything after it is ignored by the SQL interpreter.
Now, what would happen if I entered the following information into the form.

Now, when that information was returned to the database, the SQL query would look like this;
SELECT USERNAME, PASSWORD
FROM USERS
WHERE USERNAME = 'OTW' OR 1=1-- AND PASSWORD = 'anything'
When the database evaluates this statement, USERNAME='OTW" is TRUE. In addition, 1=1 also always evaluates to true. Everything after the -- (in green) is seen as a comment and ignored by the SQL interpreter, so that statement evaluates to true and you are authenticated without even using a password!
SQL Injection Characters
The more you know about SQL, the more effective you can be with SQL injection. We are making use of standard SQL commands and characters that make the database do what we want. Some of the key SQL injection characters include;
; statement termination
' or " character String Indicators
-- or # single-line comment
/*…*/ multiple-line comment
+ addition, concatenate (or space in url)
|| (double pipe) concatenate
% wildcard attribute indicator
?Param1=foo&Param2=bar URL Parameters
PRINT useful as non transactional command
@variable local variable
@@variable global variable
waitfor delay '0:0:10' time delay (often useful in blind SQL injection)
Denial of Service Attack (DoS)
A Denial Service attack can mean something quite different when dealing with databases. While most DoS attacks exhaust the existing resources so that legitimate users can't use them, with database attacks it can mean simply wiping out all the data.
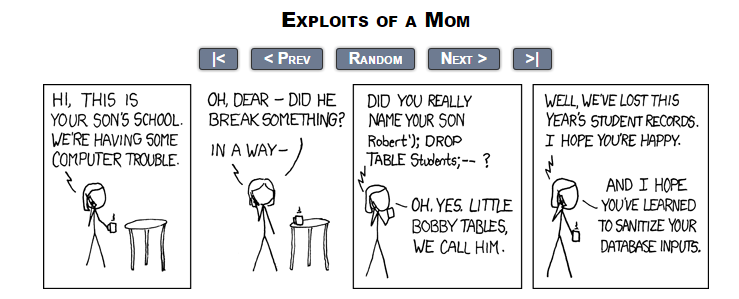
In the SQL language, rather than the command delete or remove, the keyword is DROP. To delete a table or a database, we simply need to use the keyword DROP before the object name. So, for instance if we wanted to delete the USERS table, we would say "DROP Table Users;". We could append this to our authentication form like this;

This would then create a SQL statement like that below.
SELECT USERNAME, PASSWORD
FROM USERS
WHERE USERNAME ='OTW'; DROP TABLE USERS; --PASSWORD='HackersArise"
Now, maybe the xkcd cartoon below will make more sense to you?
SQL Injection Tools
There are numerous SQL injection tools, many of them built into Kali. You can find them by going to Applications -> Database Assessment

In the order they appear in Kali;
bbqsql - This is a SQL injection tool that automates the process and can use a multi-threaded attack. It was designed specifically for Blind SQL Injection attacks (where the attacker can not see any response from the database, either errors or other output). bbqsql uses four blind SQL injection attack;
1. Blind SQL Injection
2. Time Based SQL Injection
3. Deep Blind
4. SQL Injection Error-Based
sqlmap - is probably the most popular SQL injection tool and also open source. It is designed to help you take control of a database server via vulnerable web applications. It can be used against MySQL, SQL Server,Oracle, DB2, Microsoft's Access and PostgreSQL. Among its strengths is its ability to detect the underlying database and map its table and column structure.
sqlninja - is an open source SQL injection tool that is exclusively for Microsoft's SQL Server. Only available for Linux and Unix, it is designed to help you gain access to the database and take control. It can also be integrated with Metasploit.
SQLSUS - is a Perl based, open source, MySQL SQL injection tool. Because it is written in Perl, you can add your own modules. It has the capability to clone a database into a local sqlite database on the attacker's system.This is probably the best tool for SQL injection against the ubiquitous online database, MySQL.
Havij - is an automated, Windows-based SQL injection tool. It has a user-friendly GUI making it simple to use for the beginner. It was released by the Iranian security firm, itsecteam.com in 2010.
It has very similar capabilities as sqlmap, but the user friendly GUI makes it much simpler to work with.

Safe 3 SQL injector - is an automatic tool for SQL injection with powerful artificial intelligence features enabling it to detect the database type, the best injection type and the best route to exploit the vulnerability and database. It is effective against both HTTP and HTTPS and databases from Oracle, MySQL, MS SQL Server, PostgreSQL, MS Access, sqlite, Sybase and SAP's MaxDB.
MOLE - is an open-source, automated SQL injection tool that works against MySQL, MS SQL Server and postgreSQL database servers. It is simple to use, you simply provide it the URL of the vulnerable website and it does the rest.
I will be running tutorials on each of these tools and a few others, so keep coming back my aspiring hackers!
